This is because today, almost all of the average user’s interaction with the Internet is through a browser. Even the entry point of email has become, for many, through webmail. The Web 2.0 trend only makes the reliance on HTTP even more predominant.
Times are Changing
As technologies evolve and change, so do hacking attack methods. The proliferation of the Web as the medium of choice for communication means hackers concentrate their efforts there. Network firewalls, which were once constructed to block dangerous protocols, particularly remote procedure calls (which enable programs to communicate), now find themselves helpless as these same protocols reemerge, encapsulated inside HTTP. This opens up new avenues to explore and exploit. HTTP, once merely used for text, is now a generic protocol that can transfer anything – of course text and images, but also complicated AJAX-based Web 2.0 transactions, containing sensitive data such as credit cards or other financial and personal information.
Websites – The New Battleground
The evolution of the Web medium, and the escalation in attacks, calls for different methods of defense. A traditional network firewall cannot perform the deep inspection of traffic that is now necessary. This has been capitalized upon by hackers – the amount of new HTTP-borne attacks uncovered virtually every day is staggering. From their hiding places and through distributed networks of zombies and infected proxies, hackers unleash a spate of attacks that leave no Web server untouched in their quest to infiltrate, exploit and extort.
The average website is targeted anywhere from twice to 200 times a day by miscellaneous worms and crawlers that attempt a slew of diverse attacks – some for well known exploits, others for recently discovered, and as a result unpatched, faults. Since these attacks are automated, their numbers only grow, and the attackers never tire. And the network firewalls remain inert. Traditional firewalls are really only effective to cover the third and fourth of the seven layers in what computer experts call “The OSI network model” for communication (see figure below). These are the layers dealing with establishing the network channel for communication. The content of the communication remains uninspected. This is much like knowing about a phone call – but not being able to listen in.
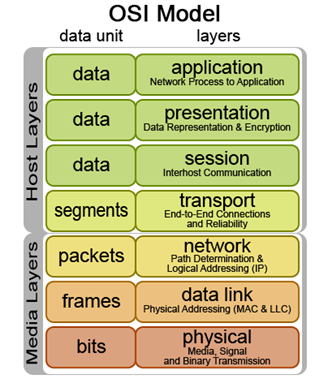
Figure 1: The OSI Network Model
A transitionary solution lies in the HTTP-sensitive firewall appliance, often provided as extra functionality in today’s high-end firewall solutions, or sold separately as a dedicated appliance. This approach is a much needed step in the right direction, climbing up the network layer and applying stronger, more intelligent rule bases on inspected traffic. An appliance, however, is still a “bump in the wire” – a middle man, and may inadvertently introduce bottlenecks or be challenged by the encrypted sessions which make up a considerable portion of today’s Web traffic.
A Better Approach
A Web Application Firewall (a.k.a. WAF), by contrast, is like placing an eavesdropping agent right next to the Web server itself – a literal “bump in the stack”. It hears what the server hears, and has final say on what it says. It serves as a two-way filter: able to prevent offending requests from reaching the Web server while, in parallel, sifting through the responses provided by the Web server, to weed out sensitive or personally identifiable information. The WAF thus serves to not only defend against attacks, but also to mitigate the potential for information leakage. The immediate proximity to the server means it is the last stop in information flow – right before the request must be served, but well after precursor steps such as encryption and fragmentation. Whereas these and other complications at the packet level pose a significant, often insurmountable challenge to network firewalls, the WAF remains blissfully oblivious to these complications, and is free to focus on what it understands so well – application level security.
The Time to Act is Now
Unfortunately, adoption of application layer security solutions by the industry has left much to be desired. Any number of valid reasons might be postulated - hardware-based solutions can be prohibitively expensive, early solutions didn’t work very well, ongoing maintenance of some technologies is time-consuming and complex, knowledge of Web application security is not widespread, and others. But the longer websites go unprotected, the more damage will be caused by malicious hackers with free reign. Considering the almost daily increase in the frequency and sophistication of attacks attempting to penetrate the application layer, there has never been a better or more necessary time to invest in protecting Web assets than right now.
Certain bodies, most notably the Payment Card Industry, now mandate Web application security as a central component in compliance requirements. Most businesses, however, remain oblivious to the threat. Fifteen years ago network firewalls were considered rare birds, and now have become ubiquitous all the way to the desktop. Soon a time will come when WAFs are considered just as mandatory. Let’s hope that by then it will not be too late for the millions of websites who are left unprotected today.
